
 4789
4789
Using Secure Run – Best Practices
Getting Started
Watch this quick video for tips on setting up Secure Run.
In addition we have a tool called Auto Rules Generator for generating rules from a machine that has all your apps.
Its in the Extras folder of the main PolicyPak download. See here for some info.
How do we setup SecureRun when each version of the software references more than one .exe to start the program?
- There is the option to Apply to Child Processes, in most cases this will elevate any other processes needed
- If not, then you will have to create rules for each process. But you can use the Auto Rules Generator to find all those .exe’s and generate rules for all quicker.

How do we setup SecureRun when there are so many variables and make them work no matter what version of the software was installed?
- Start with the AutoRules Generator to try to mass generate the rules you need.
- In Least Privilege Manager you can do a Single rule or a Combo

- For a Single many customers will use HASH to ensure its only THAT specific file that is elevated, however this doesn’t allow for future versions to be allowed
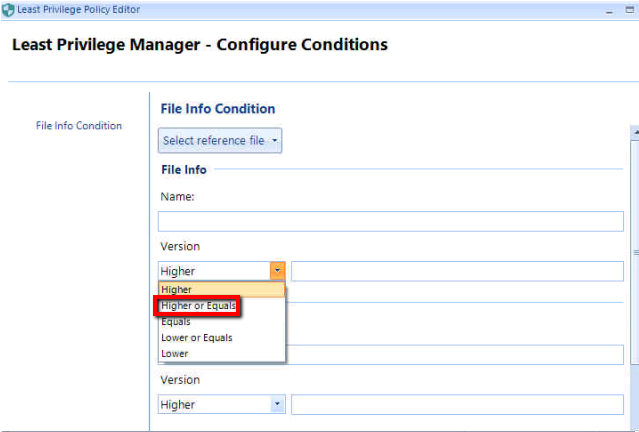
- For future proof situations, a Combo of a Signature along with File Info is often used. That way you ensure that its always that Vendor with the Signature, and with File Info you can specify to allow Higher or Equals, thereby allowing future versions to be elevated.

Summary
There are various ways to slice and dice to create the rules you want, but most common is to use Signature with File Info set to Higher or Equals and optionally Path with just filename entered (though if the app changes names often you might omit using the Path).
The more rule types you use the more secure it becomes, but keeping it usable is always the goal.
Generally only use Hash by itself because its pretty secure all alone, and then some combination of the others as noted above.


