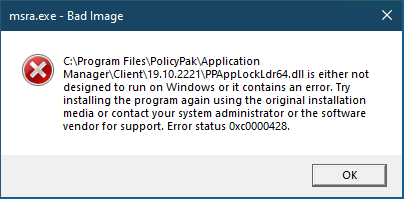
15: How to use Scripts Manager to workaround the “PPAppLockdr64.dll is either not designed to run on Windows or it contains an error” message when running Microsoft Remote Assistance (MSRA.exe) and the PolicyPak CSE is installed on Windows 10 1903

Apr 09, 2020
 5126
5126
- Create the Scripts Manager policy in PolicyPak.
- Run the Microsoft Group Policy Management Console (GPMC) as a user with the necessary rights (to create and link GPOs at that level) and then create a new GPO and link the GPO at the OU (User Level) or Domain level depending on who needs to receive these settings.
For example:

-
- Next Edit the newly created GPO and expand the User Configuration > PolicyPak > Scripts Manager section.
- Then click “ADD NEW COLLECTION” to add a new collection, give it any descriptive name you like, then click “OK”.

-
- Next, double click on the collection you just created to open the collection.
- Then right-click anywhere in the right pane and choose “Add > New Policy”, (or alternatively click on the “ADD NEW POLICY” button) to create a new policy item within the collection.

-
- The “PolicyPak Scripts Manager Wizard” will then open.
- At the “On apply action” screen choose “PowerShell script” from the drop down.
- Then paste the commands below into the scripts body window.
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass -Force
Set-ProcessMitigation -Name msra.exe -Enable DisableExtensionPoints
-
- Then check both the “Run script as user” and “With elevated rights” boxes at the bottom left hand of the window and click “Next”.
-
- Click “Next” to skip the “On revert action” screen.
- At the “Specify process mode” screen choose “Once or when forced” then click “Save”
- Lastly, test the policy.
- Log in as a domain user within the OU or Domain where the policy is applied and verify under Windows Settings that the custom Exploit Protection settings are present.

More Info: How to configure custom Exploit Protection settings under Windows 10 GUI to resolve this issue.
- Use the Windows Search to find "Exploit protection" and open exploit protection settings
- Then click "Program settings"
- Then click "Add a program to customize", and choose "Add by program name"
- Enter "msra.exe" and click "Add"
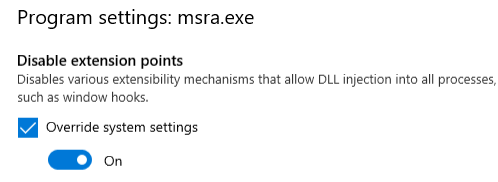
- Scroll down the list of options until you find "Disable extension points"
- Check the "Override system settings" and set the slider to "On" as in the image below.
- Lastly, click "Apply" to save your changes



